How does Keyavi uniquely protect your critical data
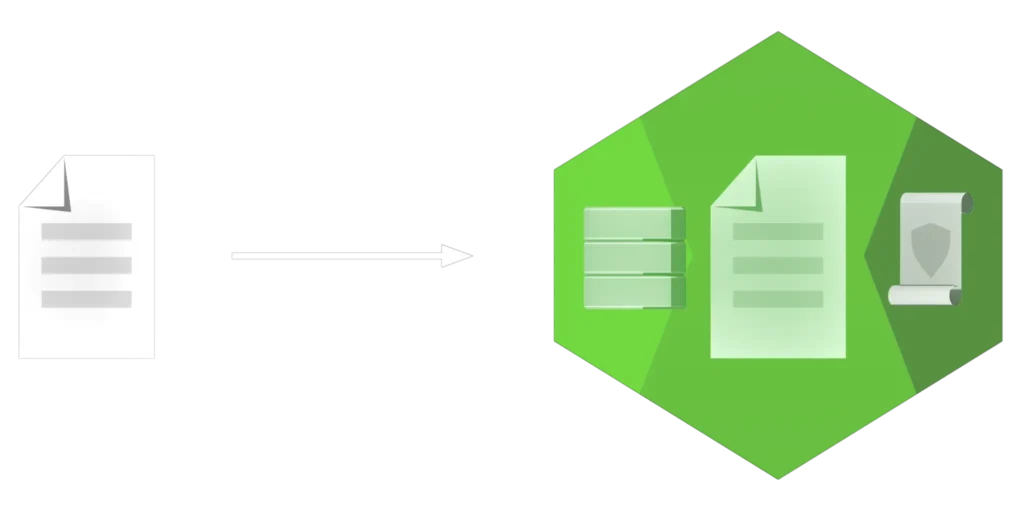
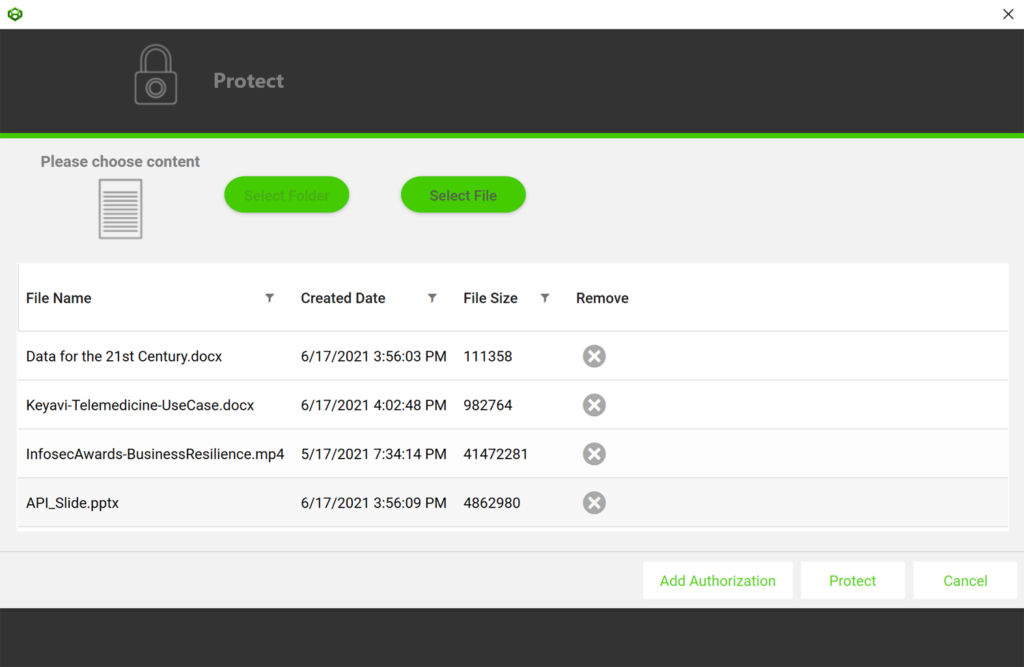
Protecting a file with Keyavi is a non-destructive process to the original document.
- The first step of the protection process places the document into an “.IKD” (Intelligent Keyavi Data) file — you can think of this as a protective wrapper.
- Next, we infuse the .IKD file with a micro-database and policies, adding a very norminal increase in file size.
- The last step in the process encrypts the .IKD file with multiple interlocking encryption keys. The default encryptions algorithm is AES 256, which can be changed by your organization if required. No encryption keys are stored in the file and Keyavi-protected files are automatically opened with the native application used to create the original document.
Harness the full power of Keyavi’s self-protecting data solution.
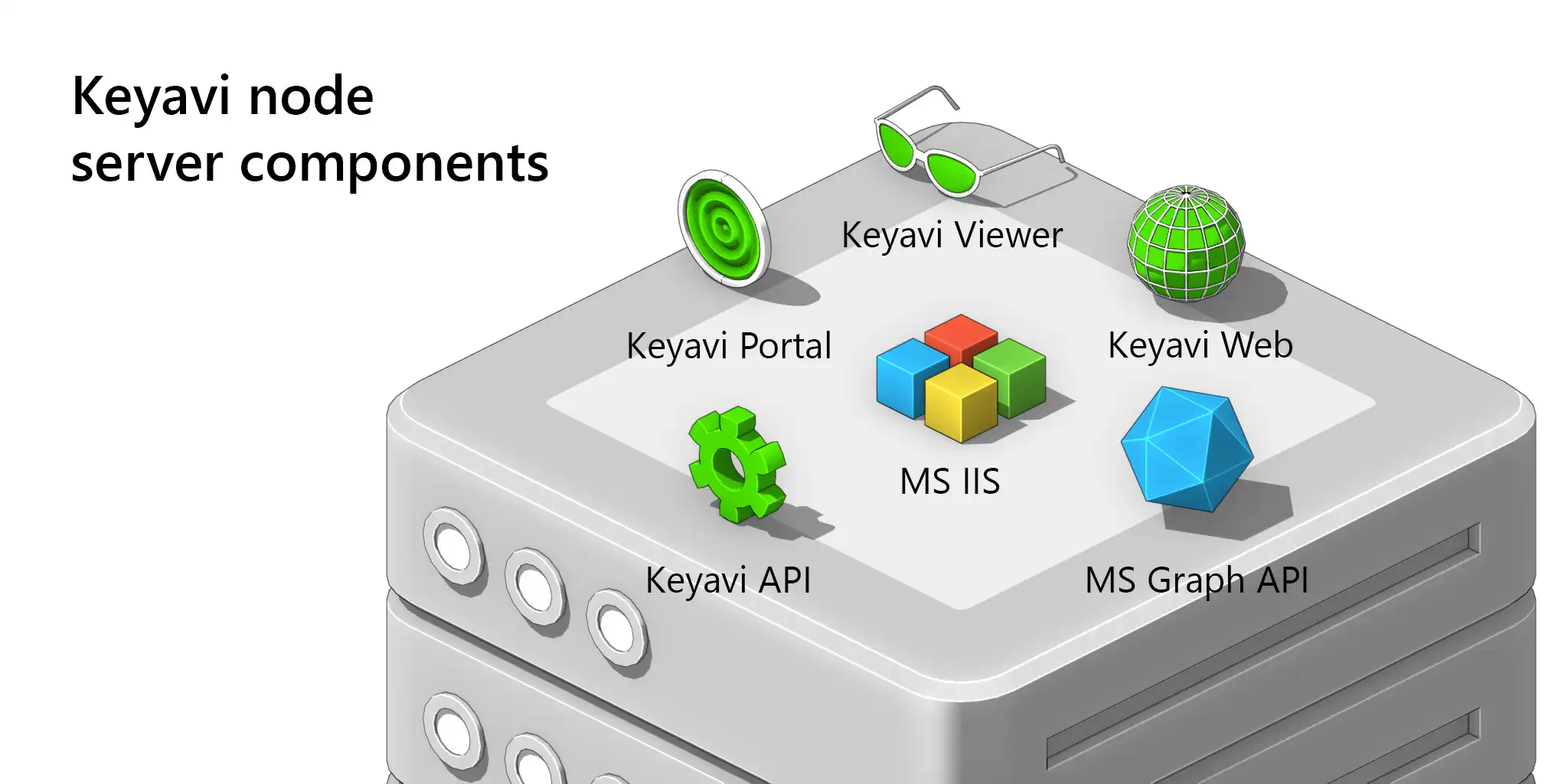
Keyavi Portal
An administrative web portal for data owners to monitor and manage their protected .IKD files. It also provides comprehensive platform controls for user, policy, and security administrators.
Demo
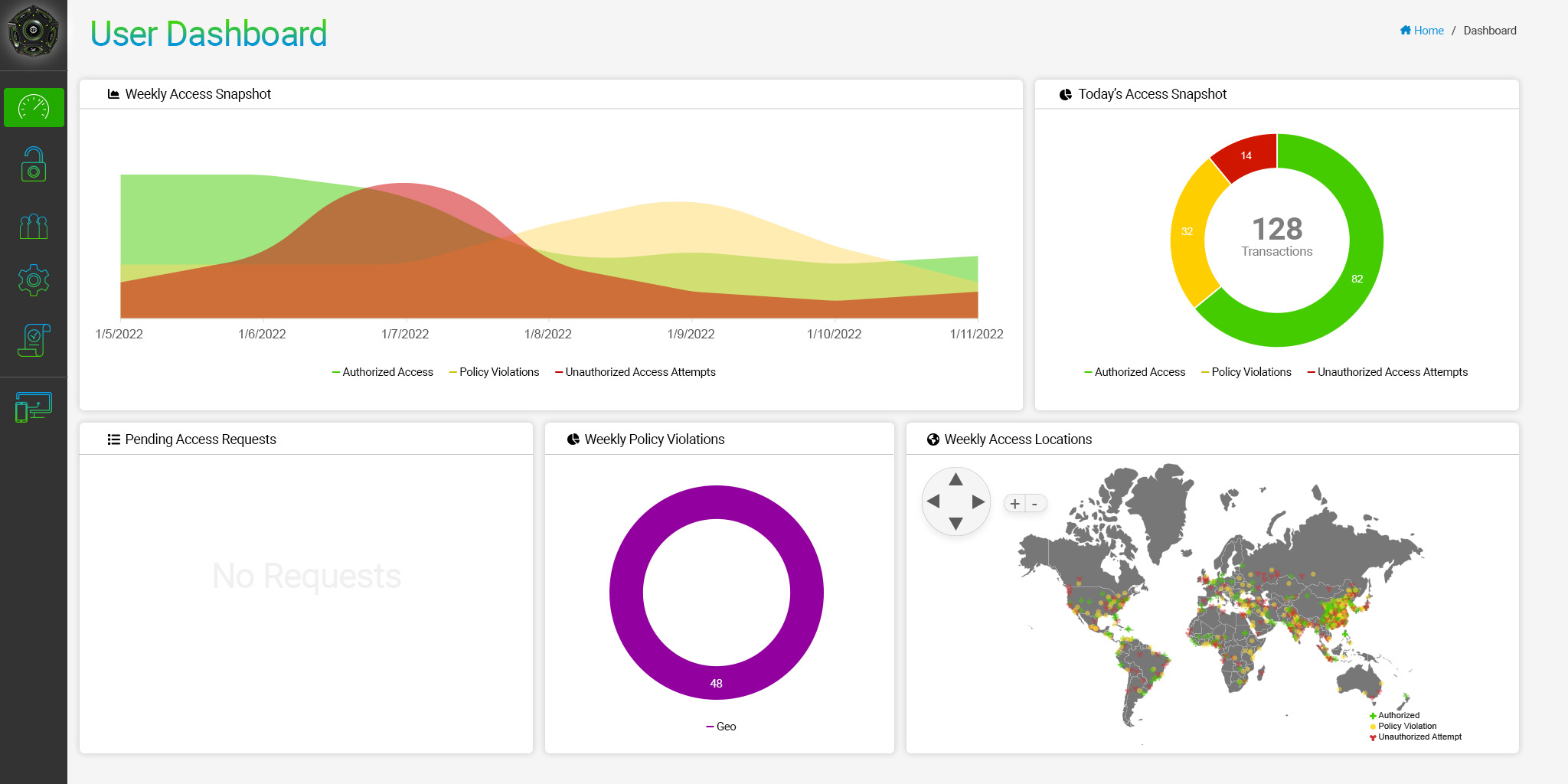
User Dashboard
Hover over a card to learn about its contents
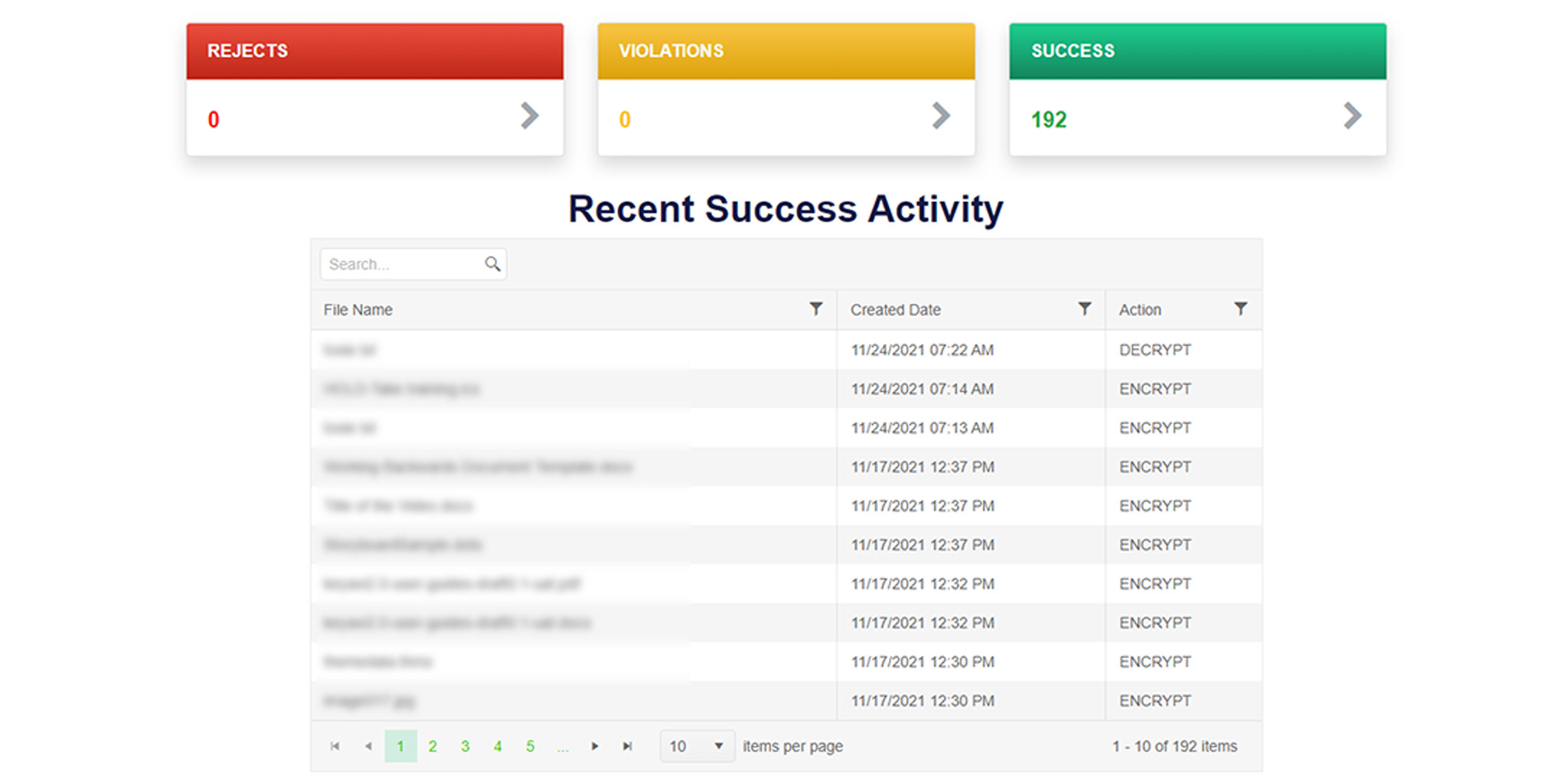
Weekly Access Snapshot
- Authorized Access
- Policy Violations
- Unauthorized Attempts
The Weekly Access Snapshot shows the trends in attempts to access the data over the past seven days.
- Authorized Access Attempts, shown in green, are successful attempts to open files by authorized users.
- Policy Violations, shown in yellow, are the number of attempts by an authorized party opening your organizations’ files but violates one or more policy conditions set by the file owner (like geolocations or time limitations).
- Unauthorized Access Attempts appear in red, and happen when an unauthorized party attempts to open the file.
Today’s Access Snapshot
- Authorized Access
- Policy Violations
- Unauthorized Attempts
Today’s Access Snapshot shows the breakdown of access attempts and potential policy violations in the last 24 hours.
Pending Access Requests
No Requests
Grant or deny access requests submitted by users who want to access secured files. Users are only able to see pending requests for the files they have secured and shared.
Weekly Policy Violations
- Geolocation
A weekly view of policy violations, including access attempts from users outside of an authorized geolocation or time access policy.
Weekly Access Locations
View all access attempts for your data from around the globe. Each pin can reveal the location and time of an Access event and whether access was granted or denied.
Data Management
Click on the top item to view data controls and records
| Name | File Type | Date Created | Is Recalled | Recalled Date |
|---|---|---|---|---|
| Financial_Projection.xlsx | .xlsx | 12/1/2022 04:24 PM | false | |
| Private_Webinar.mp4 | .mp4 | 11/26/2022 01:12 PM | true | 11/29/2022 08:05 AM |
| Company_Pii.csv | .csv | 10/19/2022 02:02 PM | false | |
| New_Chip_Schematics.pdf | 10/04/2022 03:21 PM | false | ||
| Crown_Jewels.zip | .zip | 09/12/2022 07:00 AM | true | 09/21/2022 01:45 PM |
| Proprietary_Class.cpp | .cpp | 09/01/2022 03:22 PM | false | |
| Health_Insurance.json | .json | 08/26/2022 09:09 AM | false | |
| Vulnerabilities.docx | .docx | 08/13/2022 11:04 AM | true | 08/25/2022 09:47 AM |
| Profiles.ppt | .ppt | 07/29/2022 02:56 PM | false | |
| Passwords.csv | .csv | 06/16/2022 04:45 PM | false | |
| Evidence.jpg | .jpg | 05/20/2022 08:15 AM | false | |
| Contract.pdf | 04/06/2022 03:24 PM | false | ||
| 1 15 | 1 – 12 of 12 items | |||
As a data owner, you will use the Data Management Console to recall files, modify access, add users, and add policy requirements on all the protected data you’ve created.
Click to see details, modify access, add users, or update policy requirements.
Data Management Detail Financial_Projection.xslx
Click on any card to go back to Data Management List
Access Time (shown in EST)
Access Start Time
Date TimeAccess End Time
Date TimeChain of Custody Events
| User | Date/Time (UTC) | Action | Event | |
|---|---|---|---|---|
| Webb, Jill | 01/24/2023 5:30 AM | ENCRYPT | SUCCESS | |
| 1 | ||||
Policy Audit Trail
| User | Action | Date (UTC) | Modification |
|---|---|---|---|
| Webb, Jill | Changed | 01/24/2023 12:00 PM | Access Window |
| Webb, Jill | Created | 01/26/2023 11:00 AM | Authorized Group Access |
| Webb, Jill | Changed | 02/04/2023 11:00 AM | Authorized Group Access |
| 1 | |||
Keyavi Desktop
A full-featured, user-friendly and intuitive Windows desktop solution that give users easy, secure, and complete control over their .IKD-protected files.
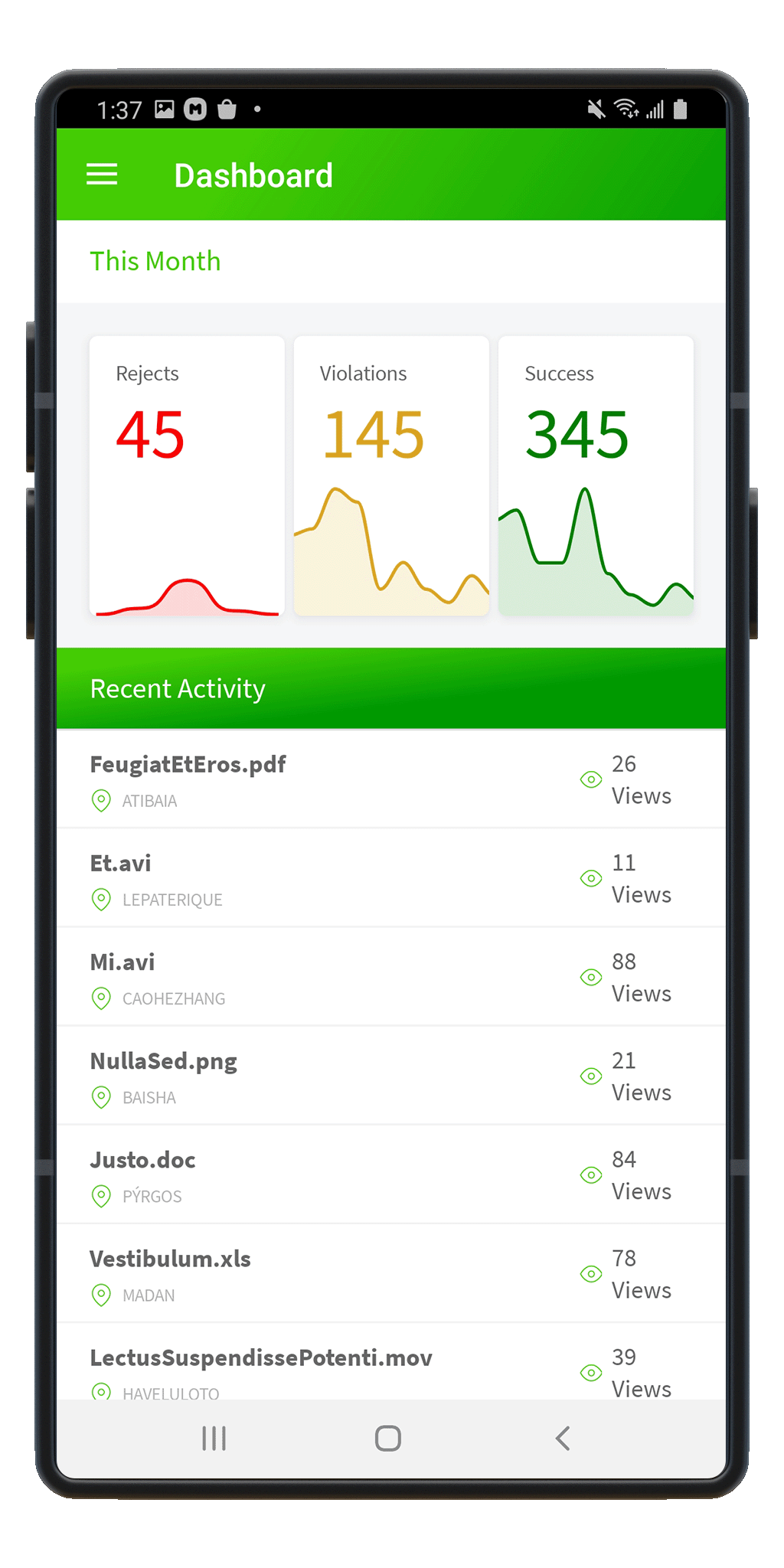
Mobile App
iOS and Android apps enable users to maintain complete control of their secured Keyavi data files on the go. You can protect files and provision access from anywhere!
Keyavi Web
Since not all users can download and install Keyavi’s technology onto their desktop, this free, browser-based web client lets users open and view .IKD files. This functionality incorporates most of the features of Keyavi’s desktop application.
Keyavi Lite
A paired-down version of Keyavi’s full desktop application that lets internal and external users open protected .IKD files in read-only mode. This free Windows app is available for download from the Microsoft store.

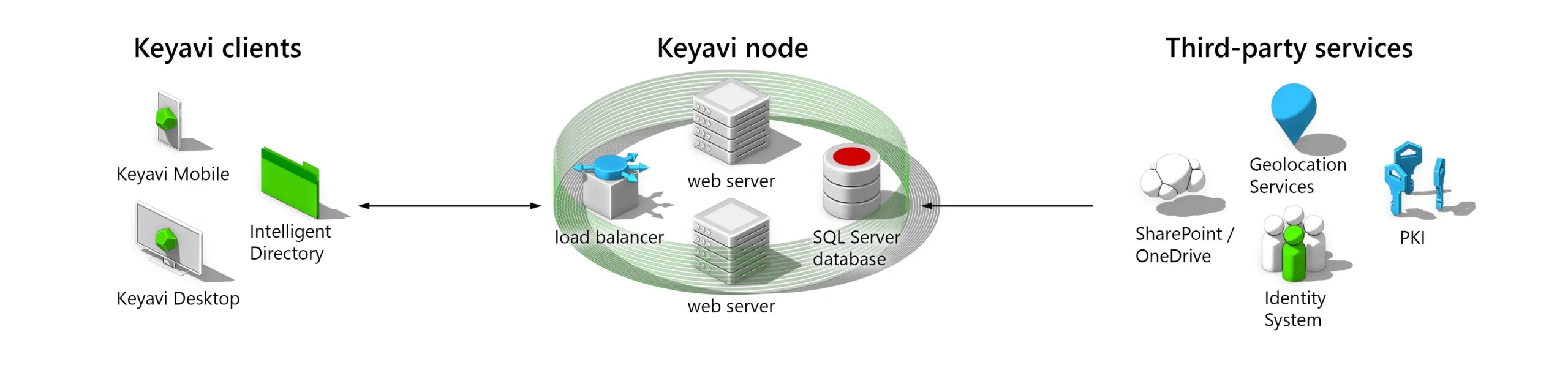
The Keyavi Service Node
The service Node is the core of the Keyavi platform. It is a RESTful API-based web service that can be installed on premise or in the cloud. The node provides management, policy and the encryption needed to protect files.